With the Sherry Singh scandal about the government allegedly sniffing our data, we should also be wondering about monitoring going on in our own home, directly on consumer level hardware.
A while back, I was trying to get admin privileges to set my Huawei router in true bridge mode to use another router as my main one.
However it seems myT doesn't allow this anymore. They only give you only a limited root access upon request. So, I started fiddling through the modem internals. I disconnected and reset'ed (with a pin) the router to revert the admin credentials to the default ones. I left it disconnected as myT reverts the config back after pinging the local ACS server as soon as it connects.
As an admin, the configuration file of the router was now available. One of the parameters in the file, 𝗫_𝗛𝗪_𝗠𝗼𝗻𝗶𝘁𝗼𝗿𝗖𝗼𝗹𝗹𝗲𝗰𝘁𝗼𝗿 has a server URL of 𝘆𝗷𝘆𝘅.𝗴𝗱.𝗲𝗱𝗮𝘁𝗮𝗵𝗼𝗺𝗲.𝗰𝗼𝗺 and a 𝐭𝐟𝐭𝐩 port of 𝟲𝟭𝟲𝟵.
<X_HW_MonitorCollector Enable="0" ServerUrl="yjyx.gd.edatahome.com" TftpPort="6169" MonitorNumberOfEntries="0" Protocol="tftp" Username="" Password=""/>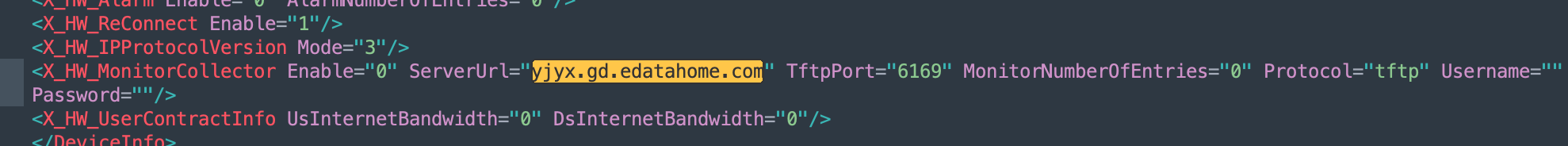
As shown in the above picture, this setting is disabled by default as the 𝗘𝗻𝗮𝗯𝗹𝗲 parameter is set at 𝟎, and the number of entries being monitored is set at 𝟬. It's disabled. All good right? TFTP is a simple protocol used to read or write a file on a server. So, is this a second sort of ACS server? But why the need for a third party server to read and write data on your router? Diagnostic, telemetry for manufacturer?
There's already the local orange.mu ACS server that can fully access your router.
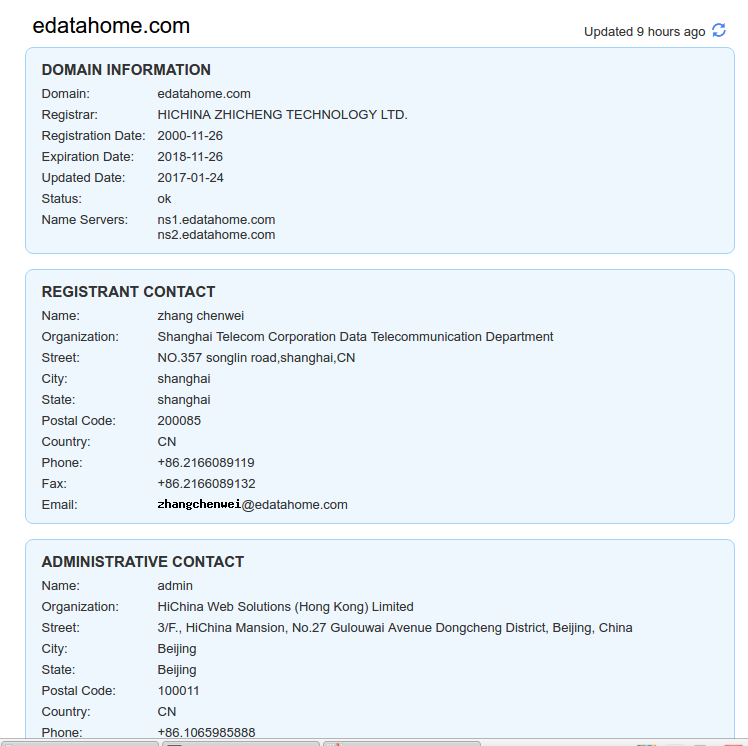
<ManagementServer EnableCWMP="0" URL="http://acs.orange.mu:1112/ACS-INTF" >A whois archived check of edatahome.com shows that, at the time, this domain was registered to 𝗦𝗵𝗮𝗻𝗴𝗵𝗮𝗶 𝗧𝗲𝗹𝗲𝗰𝗼𝗺 𝗗𝗮𝘁𝗮 𝗧𝗲𝗹𝗲𝗰𝗼𝗺𝗺𝘂𝗻𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗗𝗲𝗽𝗮𝗿𝘁𝗺𝗲𝗻𝘁. However this domain doesn't seem to be active anymore. But still this can be updated to an active server at anytime.
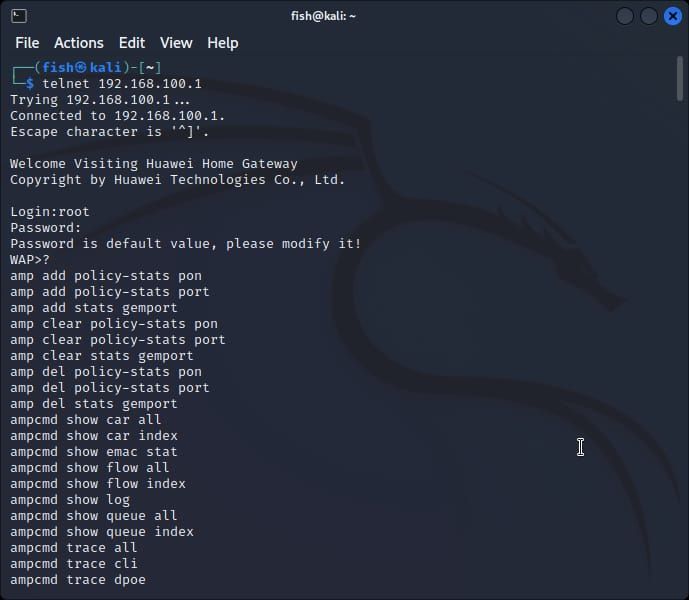
Tried to peek further inside by tunneling into router (telnet 192.168.100 root/admin), and was greeted with a WAP shell, in what seems to be Linux based but stripped down of some commands and output.
There's BusyBox installed in there but all commands are disabled except for running a bash script getcustominfo.sh.
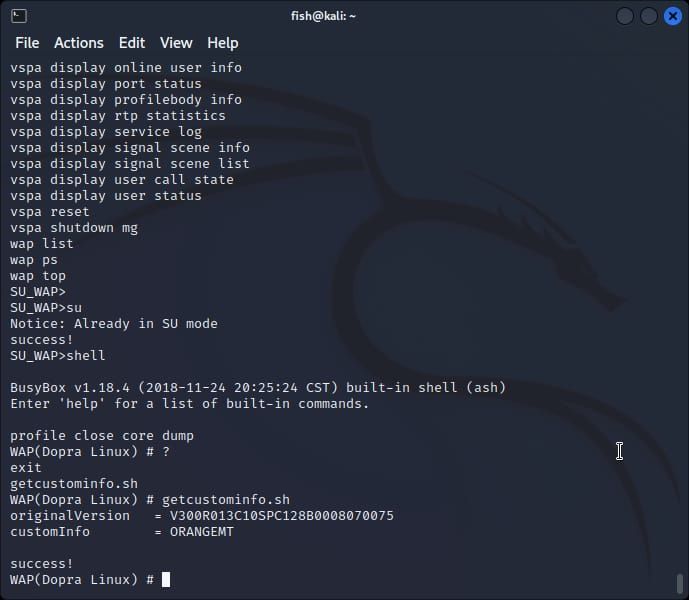
Who knows what kind of proprietary routines or backdoors are in there? Again, nothing to see here. Move along.





